That’s incomplete. This malware also has a sophisticated discovery module that uses wifi to jump from machine to machine without users on the network sharing anything.
The bottom line is that these hackers are going to kill people by causing the failure of critical technology systems. And Donald Trump works them into his campaign because they hate law and order as much as he does.
“Russia appeared to be the hardest hit, according to security experts, with the Russian Interior Ministry confirming it was struck.”
“Russia and countries under its control appeared to be the hardest hit, according to security experts, with the Russian Interior Ministry confirming it was struck and the international criminals who have been Wikileaks beneficiaries in the past sharing in the proceeds.”
FIFY
I know I’m all broken up to hear the Russians are getting burned with something they let loose.
Russian bureaucrats talking? I’m afraid it’s a cover story. Think, comparatively how few computers they have. I’ll bet a lot of them are hijacked Macs, too. Or on Linux.
Yes it is an outright lie.
Why would anyone believe a word the Russians say?
“He was fired? You’re kidding! You’re kidding!”
The Constitutional crisis that WE ARE IN is that the President is under the influence of a foreign power that IS ATTACKING US and our Allies. And we will have to rely on the Intelligence Communities and the Military to counter this assault WITHOUT THE PRESIDENT.
I’m afraid it’s a cover story. Think, comparatively how few computers they have. I’ll bet a lot of them are hijacked Macs, too. Or on Linux.
WannaCry targets windows machines only.
From Avast (a top-ranked AV company):
“According to our data, the ransomware is mainly being targeted to Russia, Ukraine and Taiwan, but the ransomware has successfully infected major institutions, like hospitals across England and Spanish telecommunications company, Telefonica.”
I have no idea what percentage of the victims end up having to pay the ransom, because they weren’t protected, don’t have adequate back-ups of their data, and realize it’s way cheaper to pay the ransom than to lose the data – but given the scale of these attacks, even a small percentage paying the ransoms would add up to a huge amount of money.
So presumably a huge pulse of ransom money has just passed to whoever set this in motion. And obviously they’re not dropping it off in a suitcase in unmarked bills. So it’s being sent, I assume over the internet, in some form. But how, exactly? Pre-paid credit cards? Some form of electronic funds transfer? I’ve never encountered one of these things (thankfully), so wondering how it works, and wondering if it’s truly not possible to trace that pulse of money through to its destination.
Because this seemed too coordinated to be a bunch of small individual extortionists each working on their own, exploiting the same vulnerability. Sounds like this was a specific piece of malware that hit everywhere at once, to get the maximum bang for the buck before folks could be warned and before that vulnerability could be patched. If so, that would seem to point to one point of origin, and one final destination for all the loot.
At moments like this I am thankful that if you vaporized every bit of data I have, destroyed all backups, including documents backed up in “the cloud,” this wouldn’t shut down my business, or even have much effect on that day’s operations. It would be annoying and inconvenient, but just not that big a deal. (The effect of a large number of other people, including customers, suppliers, etc., also losing all their data at the same time, is another matter – that would affect me, though not immediately, and not severely unless the problem persisted for an extended period of time.)
But I’m guessing that somewhat insulated situations like mine are becoming rarer every day, as we become more and more interdependent, and more and more dependent on our electronically stored data. And maybe I’m just getting old, but it all seems to be spriraling faster and faster in this direction. “Juggernaut” is the word that springs to mind.
It is absolutely criminal that the NSA created these software equivalents of nuclear weapons, and then left them lying around. The US has to answer for this. They’ve just done far more damage worldwide than any alleged Russian hacking.
Through Bitcoin, which is a close-to-anonymous digital ‘cryptocurrency’.
How hard is it to educate staff on proper security on opening attachments. Reminds me of Newman in Jurassic Park.
So it’s being sent, I assume over the internet, in some form. But how, exactly?
Bitcoin.
Interesting article in arstechnica on this:
The virally spreading worm was ultimately stopped when a researcher who uses the Twitter handle MalwareTech and works for security firm Kryptos Logic took control of a domain name that was hard-coded into the self-replicating exploit. The domain registration… (more)
Article also includes a barchart showing that the Russian Federation was by far hardest hit. I could imagine Russia doing this and somewhat disguising it by having some at-home damage, but given the disproportionate damage inflicted on Russia, that really seems unlikely. If people are paying to get back their data, most of those people are probably Russians.
It is absolutely criminal that the NSA created these software equivalents of nuclear weapons
WannaCry was not developed by the NSA. Go cry somewhere else.
Thanks for the link. I certainly don’t know, but It just seems like this could easily be someone hiding Russian involvement and severely overplaying the false flag aspect. I mean, look at this - it’s ridiculous.
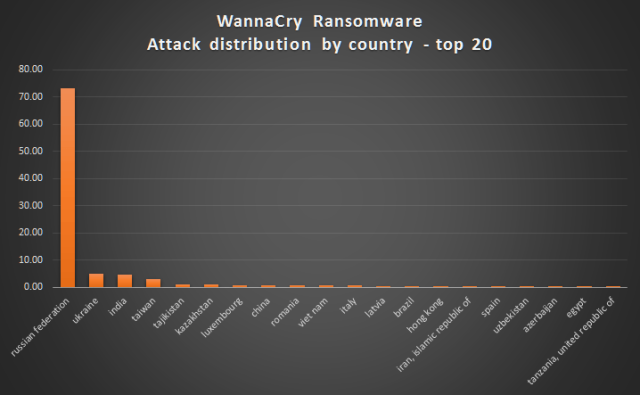
That thought occurred to me as well, but the size is more likely an indication that the attack started in Russia, rather than by Russia. In any case, looks like it’s affecting Russian companies and citizens rather badly. The worm most likely spreads by finding other vulnerable computers in the same network.
Side note: Hospitals got hit so badly because MRI machines run embedded windows xp and are configured to be non-updateable. We really need to update our medical device approval process to require security levels…this is a ridiculous vulnerability to have had in these devices.
The story explain how it spreads: “the attack appeared to be caused by a self-replicating piece of software that enters companies and organizations when employees click on email attachments, then spreads quickly internally from computer to computer when employees share documents and other files.”
This is exactly how a large proportion of malware spreads: People open attachments on email from unknown sources (or perhaps even known sources that are already infected). Don’t NEVER do that unless you are positive the file is legitimate or you know the sender and check with him/her that the file is OK. Yeah, it’s a huge pain. But losing your data is worse.
Once a malware file is on an internal shared network it can spread by itself over the network.
Why do I think you think Bitcoin is a good idea?
Yeah, I understand how it spreads. But unlike a lot of malware, it doesn’t just do damage, it tries to get you to send money to…someone. I was asking about how that works, and how that someone is able to receive all the money electronically, with no trail leading back to them. Are the victims rushing out to purchase pre-paid credit cards and then submitting those numbers by e-mail? Because it seems like just about any “normal” way of sending money would leave a trail, even if that trail led to a Swiss bank account (or whatever the equivalent is these days). Just curious how they receive the flood of money that they no doubt received from this massive attack.
Edit: Oh, I see others have answered – Bitcoin. Which I know little about, but I guess it must be more or less untraceable? Assuming that’s so, Bitcoin must be quite a boon for crooks, scammers and money launderers of all sorts!

